Implement ZTNA: Zero Trust Cybersecurity Solutions
In today’s digital-first world, protecting organizational data and applications has never been more critical. Traditional security methods, such as firewalls and VPNs, are no longer sufficient against sophisticated cyber threats. Enterprises are now turning to advanced cybersecurity solutions that emphasize identity verification, secure access, and proactive risk management.
What Is ZTNA?
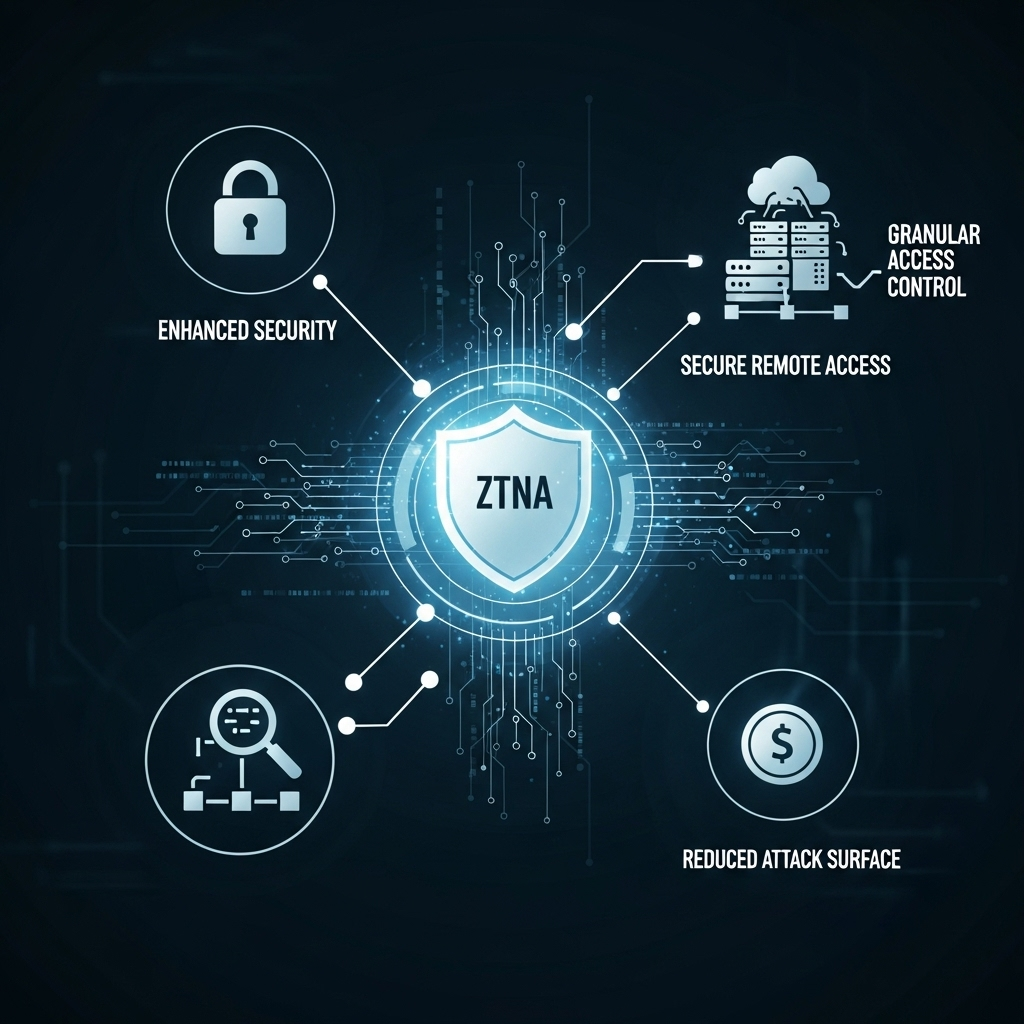
Zero Trust Network Access, or ZTNA, is a modern security framework that ensures users can access only the resources they are authorized to use. Unlike traditional security models that trust users inside the network perimeter, ztna verifies every access request based on user identity, device health, location, and real-time risk assessment. This “never trust, always verify” approach drastically reduces the attack surface and prevents unauthorized access.
Why Businesses Should Implement ZTNA
With more employees working remotely and cloud adoption increasing, businesses face new security challenges. Implementing ZTNA ensures that sensitive data is protected while allowing employees to work securely from anywhere. By limiting access to only what is necessary, ZTNA reduces the risk of data breaches and insider threats, making it a critical component of modern cybersecurity strategies.
Key Features of ZTNA Solutions
Top ZTNA solutions provide features like identity-based access control, application segmentation, encrypted communication, and continuous monitoring. These features ensure that only verified users can connect to specific applications, preventing lateral movement of attackers within the network.
Integration With Cybersecurity Services
For maximum effectiveness, ZTNA should be part of a broader suite of Cybersecurity services. This includes endpoint protection, threat monitoring, identity management, and compliance support. Integrating ZTNA with these services creates a layered security approach that strengthens an organization’s overall defense and prepares it for future threats.
Benefits of Implementing ZTNA
-
Enhanced Security: Grants access based on identity and context, reducing risk.
-
Seamless Remote Access: Employees can work securely from any location.
-
Regulatory Compliance: Supports data privacy and security requirements.
-
Scalable and Flexible: Adapts to evolving business needs and cloud adoption.
Conclusion
Implementing ZTNA is no longer optional for businesses looking to secure their digital assets. By combining Zero Trust principles with advanced cybersecurity frameworks, organizations can protect sensitive information, streamline secure access, and stay ahead of evolving threats. ZTNA provides a practical, future-ready solution that strengthens any cybersecurity strategy.
- Arte
- Causas
- Artesanía
- Bailar
- Bebidas
- Película
- Fitness
- Alimento
- Juegos
- Jardinería
- Salud
- Hogar
- Literatura
- Musica
- Redes
- Otro
- Fiesta
- Religión
- Compras
- Deportes
- Teatro
- Bienestar